The post Effortless Scaling, Real Savings: Why Serverless Computing Is Revolutionizing the Web appeared first on Annexbyte.
]]>What is Serverless Computing?
Think of it like a cab service that appears at a snap of your fingers, ready to whisk you away without the hassle of ownership. Serverless computing mirrors this on-demand convenience for your digital needs, offering a seamless, pay-for-what-you-use approach that adapts resourcefully to your website’s live audience.

Why Businesses Are Paying Attention to Serverless
Businesses are flocking to serverless for some pretty convincing reasons:
- Cost-Effectiveness: The serverless model is a financial game-changer. It’s like paying for just the water you drink, rather than the whole well. By only billing for the resources utilized, serverless computing puts a full stop to wasteful spending.
- Simplified Operations: Say goodbye to the endless cycle of maintenance and updates. Serverless takes the back-breaking server management off your plate, freeing your team to innovate and excel where it truly matters.
- Scalability: Serverless is like a beanstalk that grows to the clouds or shrinks to a sprout exactly when needed. This nimble scaling means your site can handle traffic surges without breaking a sweat.
- Eco-Friendly Footprint: By maximizing resource efficiency, serverless computing is a nod to a greener planet, reducing the energy drain associated with idle servers.
How to Get Started with Serverless?
If you’re intrigued by the serverless buzz and wondering how to jump on the bandwagon, you’ll be pleased to know that getting started is as easy as pie. Here’s how you can roll up your sleeves and begin your serverless adventure:
Step 1: Find Your Serverless Playground
The first thing you need is to choose where you’ll build your serverless application. Think of it as picking out the perfect lot to build your dream home. You have a few good neighborhoods to choose from—AWS Lambda, Azure Functions, and Google Cloud Functions are some of the popular spots. Each offers its own set of tools and toys to play with, so pick one that seems most welcoming and has the most helpful guides and tutorials for beginners.
Step 2: Take the Guided Tour
Just like visiting a new city, you’ll find guided tours immensely helpful. Each serverless platform comes with its own set of tutorials. These are like your travel guidebooks, showing you the sights – or in this case, teaching you how to deploy your first piece of serverless code. It could be something simple like a function that sends an email when someone fills out a contact form on your site.
Step 3: Guide Your Project with Training Wheels
Now that you have the lay of the land, start with a tiny project. Think of it as your first garden—small, manageable, but full of potential. A great starter project is a serverless image-resizing function—every time you upload a photo, it automatically adjusts it to the perfect size for your website.
Step 4: Grow Your Community Roots
Remember, even if you’re new to the neighborhood, you’re not alone. There are plenty of serverless meetups and online forums. Joining these communities is like having a neighborhood block party where everyone shares their best recipes—only these recipes are for code!
Step 5: Expand Your Construct with Confidence
With a bit of experience under your belt, you can now expand your project or start new ones. Maybe you’ll build a serverless backend for a mobile app or a system that processes payments for your online store. As your confidence grows, so can the complexity of your projects. Remember, the sky’s the limit!
Step 6: Stay Vigilant and Keep Learning
Just as with any new endeavor, there will be learning curves and potholes to avoid. Keep a keen eye on the costs of your serverless architecture and always prioritize securing your applications. As the serverless technology evolves, keep updating your skills through continuous learning.
Real-Life Magic with Serverless:
Here’s where theory meets practice: real businesses making serverless work for them.
- A travel agency uses serverless to only run their booking system when someone is using it, cutting down on costs during off-peak times.
- A food delivery app manages orders by spinning up serverless functions to match demand during lunch and dinner rushes, and scales down when it’s quieter.
These aren’t just hypothetical scenarios; they’re actual cases where serverless computing is making operations smoother, more scalable, and cost-effective.
Wrapping It Up
Starting with serverless doesn’t require you to be a tech whiz or a large enterprise. It’s for anyone looking to simplify their web services and embrace a future-proof way of building on the web. By following these steps and looking at how others are doing it, you’re on your way to enjoying the benefits of serverless computing: more time to focus on what matters and less on the technical heavy lifting.
The post Effortless Scaling, Real Savings: Why Serverless Computing Is Revolutionizing the Web appeared first on Annexbyte.
]]>The post Significance of Email SPF DKIM Records – How it could be the reason emails are going to the spam appeared first on Annexbyte.
]]>Authentication is the key. While delivering an email, you need to ensure that your email seems authentic enough to pass through the ISP filter gates easily. Each email sent must pass different authentication levels, which is done using DKIM and SPF. Before understanding what significance they have, let’s understand what it is.
What is an SPF Record and Why Is It Important?
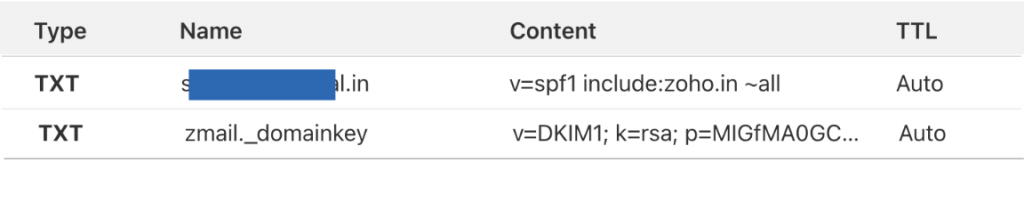
SPF is the short form of the Sender Policy Framework. It is a protocol used for validating emails and is specially designed to first sense and then block any type of email spoofing, phishing, or spam. It is pretty simple: through this, the mail exchangers know for a fact that the email is coming from a reliable source.
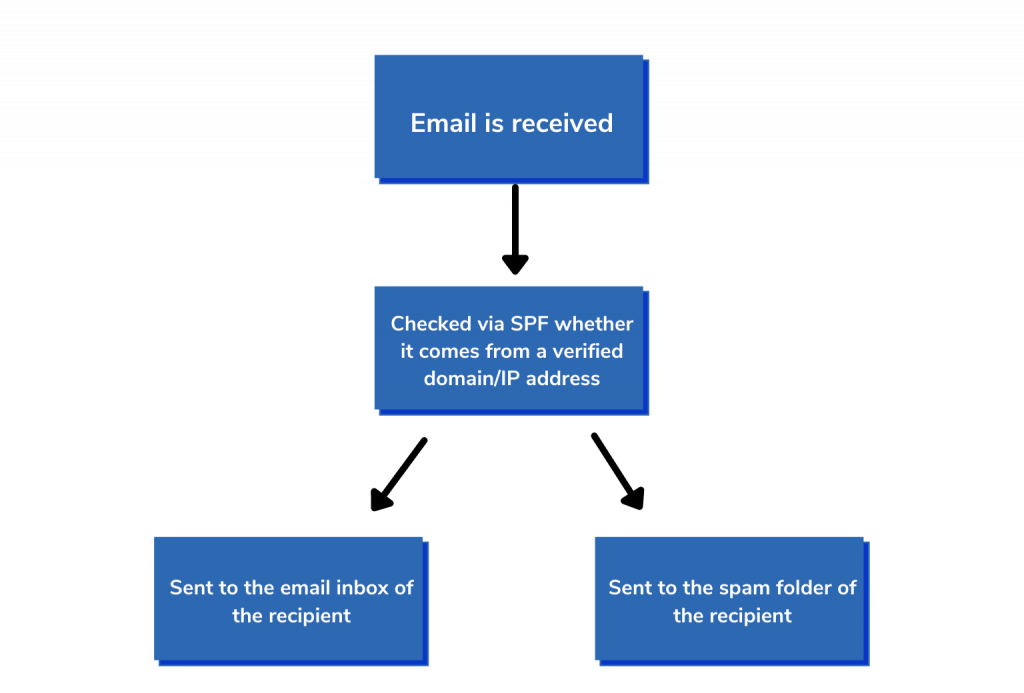
This is ensured by checking the IP Address and the domain. If the domain comes from an authorized IP address (through the administrators of the specific domain), it is allowed to go ahead. It is in the form of a TXT record and can be found in the Domain Name System (DNS). The DNS has all the servers and IP addresses that are allowed to send an email from a particular domain.
Once you send an email out, the ISP checks the return path of the domain before anything else. This is a straightforward and foolproof way to ensure it is not spam. The IP address of the incoming email and the registered domains are cross-checked to ensure it is not spam.
Why Do I Need To Include An SPF Record?
Sure, there is no obligation to set up an SPF record. But, having an SPF policy will make your email more trusted, and the probability of your email reaching your recipient’s inbox will increase. The easiest way is to use an SPF builder to make a list of domains that are authorized to send an email from you. This will allow you to make an SPF record of all the domains.
What Is A DKIM Record And Why Is It Important?
DKIM is the short form of Domain Keys Identified Mail. This security measure is put forth to ensure that the message in the email being sent is not changed after being sent and before being received. It works by using cryptography to assign private keys through public keys to each message. The public key is used by the server getting the email message to make sure that the DNS of the domain is the actual source of the message.
This makes sure that the message has not been tampered with at any level. This verification process leads to the completion of the DKIM process and allows the email to enter the recipient’s inbox as it shows that it is authentic.
Why Do I Need To Include An DKIM Record?
Again, DKIM is not a requirement that will ENSURE that your email won’t end up in the spam folder. But, it will increase the chances of your email ending up in the inbox rather than in the spam or junk folder. DKIM usage does not allow email spoofing, and it gets harder and harder if an email is marked with DKIM. Most of the popular ISP’s like Gmail, Yahoo, and AOL all use it as a tool to see if the email is from a reliable source or not. It is mostly used with SPF to give additional layers of security to the email.
Value of DKIM And SPF Together
For businesses that frequently send transactional and commercial emails, we recommend you incorporate both SPF and DKIM. The advantages are two-fold. First of all, your business will stay safe from spoofing and phishing attacks. On the other hand, your brand reputation and customer relationship will also increase.
Wrapping Up
Both SPF and DKIM records will provide a layer of authentication to your email. Moreover, if properly done and introduced, they can also increase and improve the deliverability and in turn increase business revenue.
The post Significance of Email SPF DKIM Records – How it could be the reason emails are going to the spam appeared first on Annexbyte.
]]>